Joe Sandbox View - the threat hunting & search engine
Joe Security's Blog
Published on: 08.08.2017
Hunting for similar or associated threats is a key task for SOCs, CERTs, CIRTS and IR teams. If you are testing threat search engines, you will find many allowing searching for a very small set of IOCs, mostly:
- File hashes (MD5, SHA1 etc)
- IPs
- Domains
- Names of dropped files
What if you want to search for more detailed, deeper and low-level information? Well, you reach a dead end, but fortunately, there is a solution now - Joe Sandbox View.
Joe Sandbox View explained
Joe Sandbox View is a search engine based on Elasticsearch, that is fed by Joe Sandbox Cloud Pro (customers can opt-in to share their analyses) as well as Joe Sandbox Cloud Basic.
The average amount of data added per report is 20 MB.
Data populating Elasticsearch includes:
Data populating Elasticsearch includes:
- Detection status
- Score, Confidence, Label
- Full static file information
- PE, APK, MACHO, IPA, DOCX, OLE, etc.
- Full behavior signatures information
- Spreading, evasions, phishing, exploiting, Trojan activities, spyware activities, banking, spamming, etc.
- Full system behavior
- Created, modified, written, read, deleted files
- Created, modified, read registry keys
- Created, stopped processes
- Allocated, written and read memory
- Created mutexes
- Connected, bound sockets
- Loaded modules
- Created, modified, terminated, delayed threads
- Etc
- Full network analysis
- HTTP gets, posts with raw & encoded bytes
- FTP
- SMTP
- DNS
- ICMP
- IRC
- TCP & UDP connection data
- Inspected HTTPS
- HTTPS certificates
- Code manipulations
- IAT, EAT, SSDT, IDT, DKOM, inline hooks etc
- Performance statistics
- CPU, Memory
- Hybrid Code Analysis data
- Executed functions
- Non executed functions
- All APIs, instructions, strings per function
- Antivirus detections
- Virustotal and Metadefender
- For dropped files, domains, initial sample
- Yara detections
- For dropped files, PCAP, initial sample and memory dumps
The information is rich and enables users to do very advanced searches. The above list is just for analysis on Windows. However, also data from Android APK analysis and Apple Mach-O analysis are fed into Joe Sandbox View.
Joe Sandbox View Interface
Joe Sandbox View is very simple to use. If you log in, you can either choose one of the predefined searches or you construct your own query:
If you want to construct your own query, click on Add Filter. You can then select one of 1,500 identifiers or fields (compare this number to other threat/intelligence searches) :
For each field you can select from various comparison operators:
The operators vary on the search field type, as an example, for numbers, operators such as =, >, < are available.
What if you want to search for contextual data?
For example, let's assume you want to search for all samples where there is a process called "explorer.exe" which created an EXE file in the temp directory.
This can be done via nested queries. To do so, select the "process" node (nodes are tinted blue):
For example, let's assume you want to search for all samples where there is a process called "explorer.exe" which created an EXE file in the temp directory.
This can be done via nested queries. To do so, select the "process" node (nodes are tinted blue):
Then a new filter level opens. It displays the nodes and fields you can select from within the same process context. Of course, multiple nesting is possible as well, as shown here:
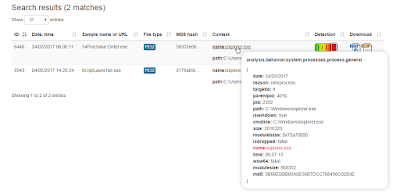
Another very interesting feature is that Joe Sandbox View also provides context information for each search so that you can see e.g. what the MD5 hash of the created file is. To view or download the full analysis report, just click on the icons on the right.
Joe Sandbox View Example Searches
Given the abundant data & the nice and simple search interface one can easily do very complex queries:
- Generic Locky query, based API calls and strings in a disassembly function context
- List all Office Documents, sample calling PowerShell in VBA Macro code based on dynamic VBA data extracted via VBA instrumentation
- Listing all malicious OpenXML Office document samples which connect to Russia, based on OLE extraction and network analysis
As the examples show the number of searches & combinations is unlimited.
Joe Sandbox View Context for Joe Sandbox
Joe Sandbox View not only has a UI but also an API. Via the API Joe Sandbox enriches its analysis reports with additional context information. It creates lists of all associated samples based on:
- IPs
- ASN (Autonomous System Number)
- Domains
- Dropped files
Hereby incident responders get a quick overview of associated or similar samples. Let us have a look at the recent analysis of a malicious Javascript file (MD50b185422af3ce8629a384d497e1c3c33). From the behavior graph we see the sample connected to IP 47.91.93.208 which has been registered by AlibabaChinaTechnologyCoLtd:
With the View integration one can now easily see all other/associated samples which also connected to an IP from AlibabaChinaTechnologyCoLtd:
For each find correlated data is shown. For ASN this is the IP, for Domain the IP and for IP it is an HTTP URL:
Joe Sandbox View is available in Joe Sandbox Cloud Pro since January 2017.
With the View integration one can now easily see all other/associated samples which also connected to an IP from AlibabaChinaTechnologyCoLtd:
For each find correlated data is shown. For ASN this is the IP, for Domain the IP and for IP it is an HTTP URL:
Conclusion
With Joe Sandbox View we make the massive amount of behavior captured by Joe Sandbox searchable. Searching is easy since the interface is simple and intuitive. Very advanced searches are possible for over 1,500 different values/fields. Via the API Joe Sandbox directly benefits from the threat intelligence data of View.
Joe Sandbox View is available in Joe Sandbox Cloud Pro since January 2017.