
Joe Sandbox Cloud

ML Engine to detect unknown malicious Files.
Joe Sandbox ML does not require any signature updates to detect unknown malicious files.
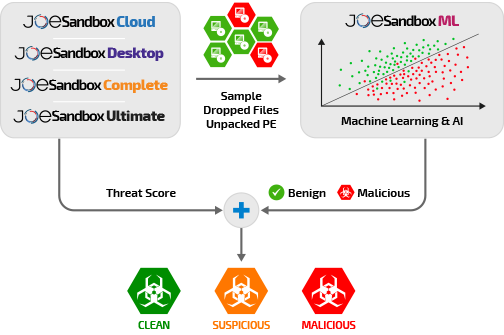
Joe Sandbox ML is a plug-in which integrates seamlessly into Joe Sandbox Cloud. With Joe Sandbox ML, Joe Sandbox Cloud benefits from enhanced detection capabilities in cases where dynamic analysis does not reveal any malicious behavior.

Joe Sandbox ML Explained
Joe Sandbox ML is run on function traces gathered by Joe Sandbox during execution. This not only includes executables but also installers and common script types like PowerShell. By leveraging advanced analysis techniques, Joe Sandbox ML ensures that a wide variety of malware entry points are thoroughly examined. For all these files, Joe Sandbox ML will generate a verdict which is either clean or malicious. Joe Sandbox ML's verdict is then combined with the threat score determined via the dynamic execution. The final verdict is shown to the user, providing a detailed and reliable assessment of the sample's behavior and intent.
Joe Sandbox ML greatly helps to detect malware samples which do not show much behavior during the dynamic execution. By combining static with dynamic function traces, even crashing samples or DLLs can be effectively analyzed, enabling the detection of malicious intent and characteristics that might otherwise be missed. This comprehensive approach ensures no detail is overlooked, offering robust analysis for sophisticated threats that may evade traditional methods.
Learn more about Joe Sandbox ML
Contact Joe Security to schedule a technical presentation.
State-of-the-Art Deep Learning Analysis
Joe Sandbox ML employs cutting-edge deep learning techniques to scrutinize executable behaviors, analyzing Windows API calls and static PE data for precise threat detection.

Beyond Standard Executables
Joe Sandbox ML provides advanced detection across a wide range of file types, not limited to PE files. From MSI and JAR to PowerShell and Batch scripts, Joe Sandbox ML identifies threats in diverse executable formats.

High Detection Precision
Joe Sandbox ML is tuned to detect as many malicious samples as possible. In addition, Joe Sandbox ML results have a low false positive rate.
High Performance
Joe Sandbox ML provides a verdict very quickly, often under one second. This allows to analyze thousands of files very quickly.

Learn more about Joe Sandbox ML
Contact Joe Security to schedule a technical presentation.
